Independently conducted by the Ponemon Institute, and based on quantitative analysis of 524 recent breaches across 17 geographies and 17 industries, the annual cost of a Data Breach. The average cost of a data breach has fluctuated between $3.50 million and $4.00 million in recent years. Nearly half of said breaches resulted from a malicious attack, and the rest happened because of system glitches and human errors.As you can imagine, we don't need to highlight the importance of an organization's security since everyone is aware of its consequences. We never had so many clients submitting their so-called "Penetration Test" to us for review in the last twelve months.
Penetration testing (which is also sometimes called pen testing or ethical hacking) refers to the security process of evaluating your computer system's applications for vulnerabilities and susceptibility to threats like hackers and cyberattacks. Examples of vulnerabilities include software bugs, design flaws, and also configuration errors.
To ensure more security for your DALIM ES system, you can put in place a Single Sign-On Authentication (SSO) coupled with multifactor authentication, as we will explain below with OneLogin.
This page will help you to go through the initial setup of DALIM ES with the OneLogin Single Sign On solution.
OneLogin has capabilities to source the users from an Active Directory such as DALIM ES.
The most interesting part that you can enable Multi Factor Authentication in OneLogin to improve the access security to your DALIM ES solution.
We will use the OpenID protocol to enable the SSO.
In our example, we are using our Azure AD directory to source some sample users to Onelogin.
If you wish to import automatically your users from your Azure AD, please follow at first this procedure prior to setup the Onelogin SSO:
Azure AD Authentication with DALIM ES 6 and upward
1- Create the User Directory in OneLogin
The first step will be to source the users of your Active Directory to OneLogin
For this, go to the Users/Directories menu of OneLogin and create a new Directory "DALIM Azure AD TEST" for example.
You will wish to import the users from your Azure Directory.
The tenant ID is an information that you will find in your Azure AD setup page.
Once you have entered it, you will need to click the button below the tenant ID to enable the connection between OneLogin and Azure AD.

You can save these first settings.
The Directory Attributes can be left as is as we will use the "preferred_username" standard field for making the matching between the AD user name and the ES user name.
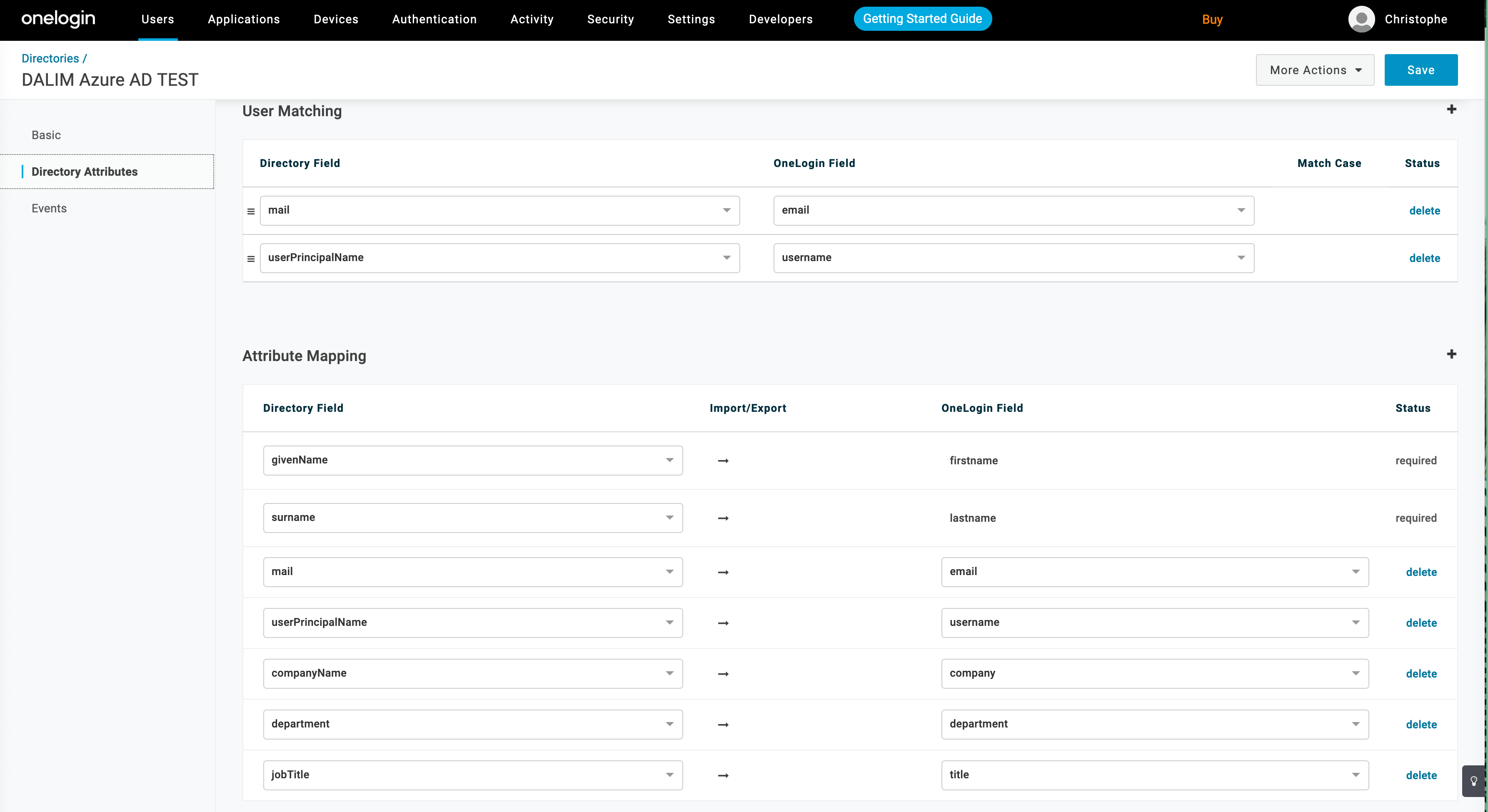
Once the setup is saved, you will see that some users have been imported (6 on our example).
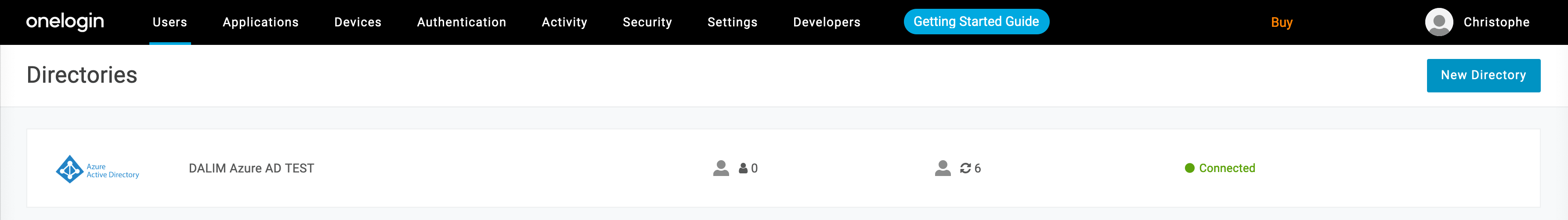
2- Create an application for DALIM ES based on OpenID
Under the Applications tab one OneLogin, you will have to create an application.
Here, we are interested in connected DALIM ES with the OpenIDC protocol, therefore in the list of apps, please search for "openid" and choose the "Openid Connect (OIDC)" application from OneLogin Inc
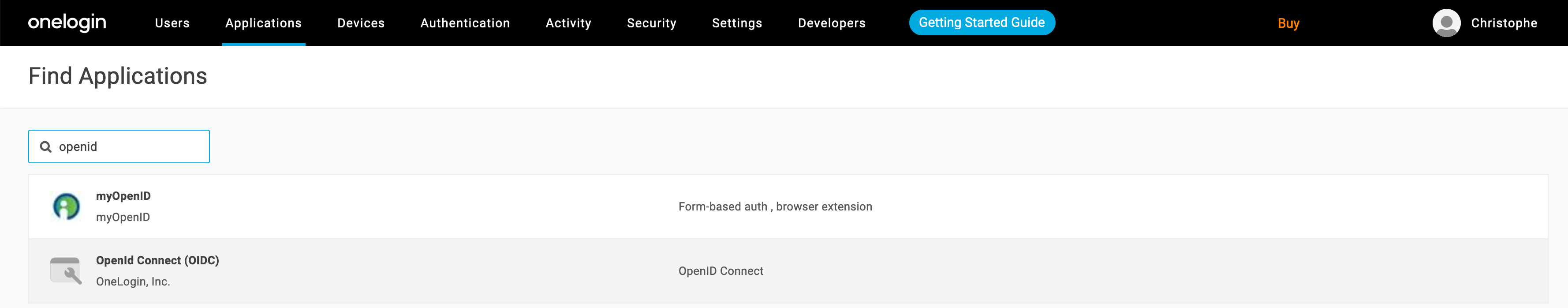
Start by giving a name and description to your Application
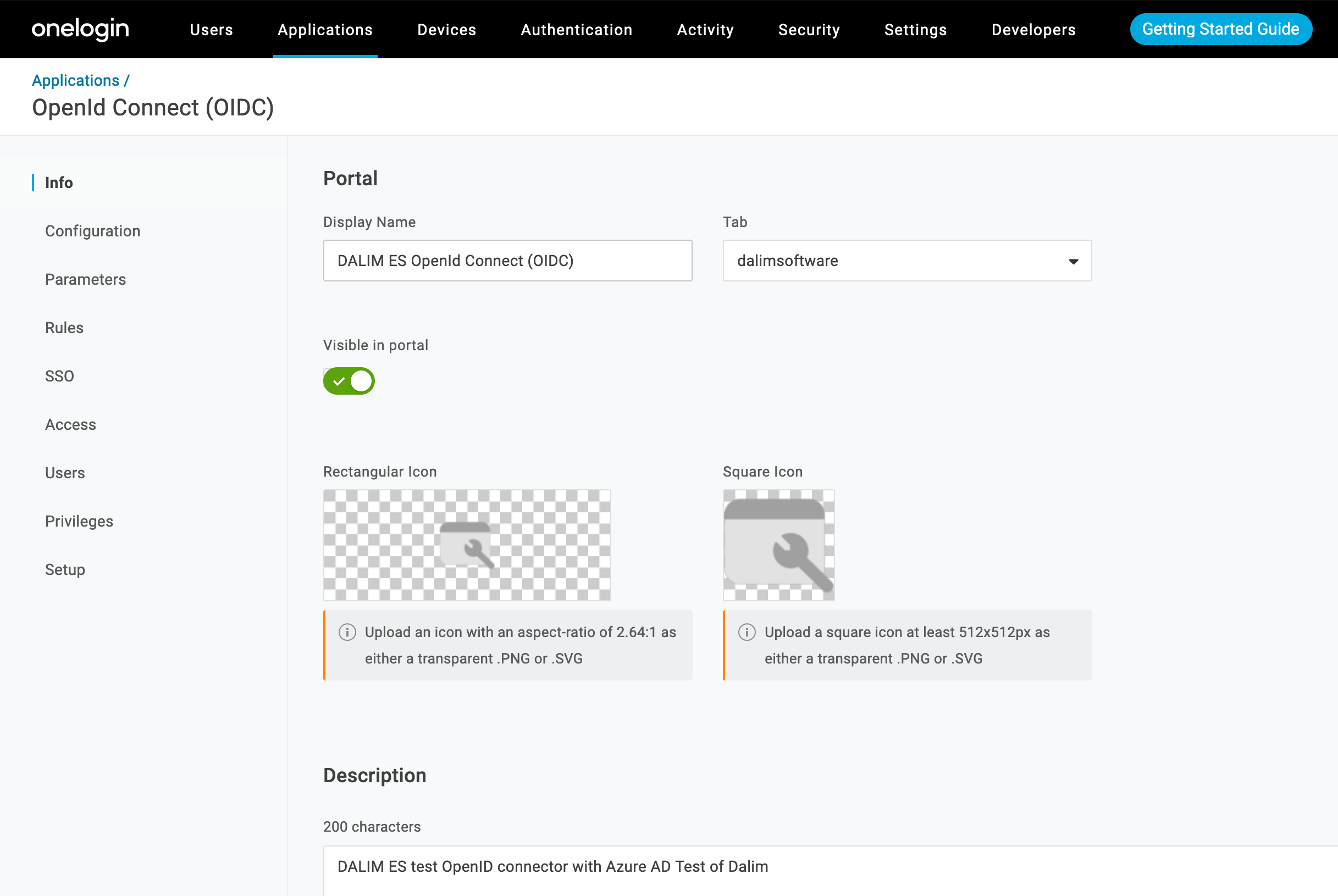
As second step, please fill up the URLs under the Configuration tab:
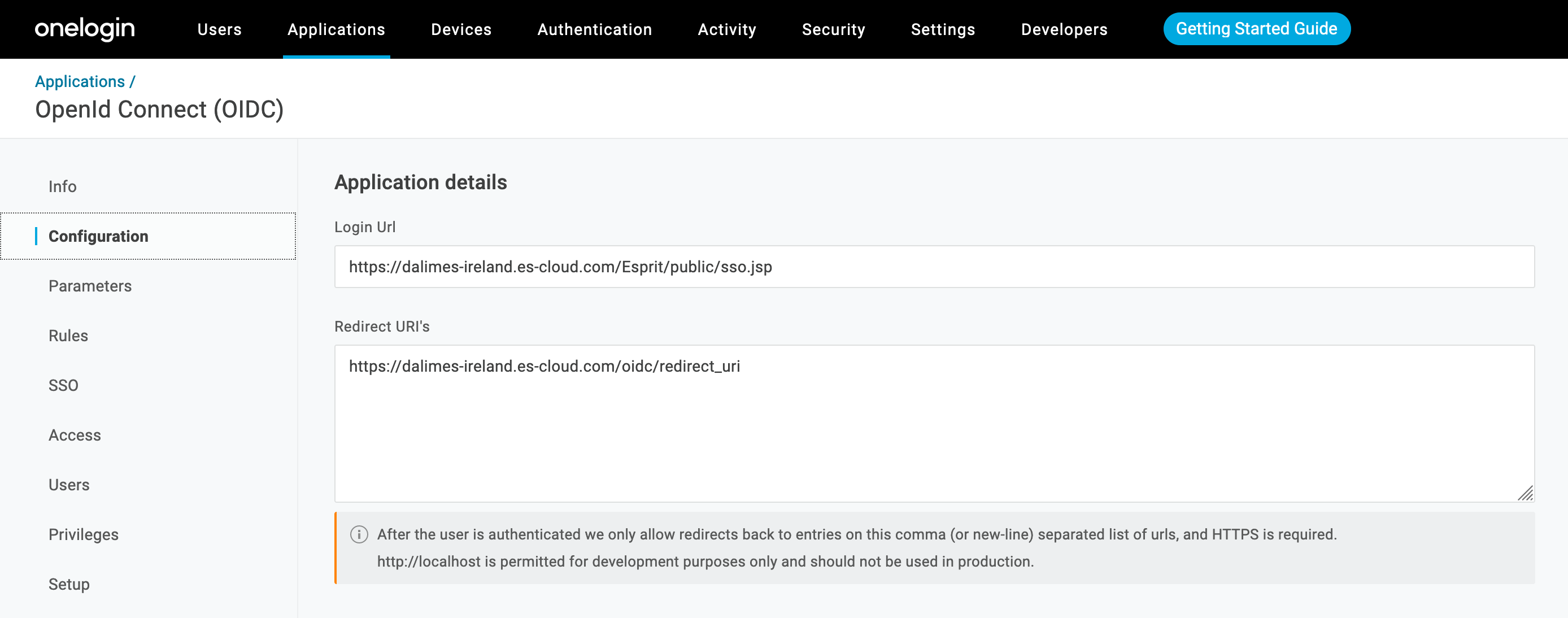
For Login Url we will use:
https://dalimes-ireland.es-cloud.com/Esprit/public/sso.jsp
For Redirect Url we will use:
https://dalimes-ireland.es-cloud.com/oidc/redirect_uri
Both URLs will be used at step 3. for the Apache setup
As next, go to the SSO tab to get the Open ID parameters which will be used as well for the Apache OpenIDC module setup.
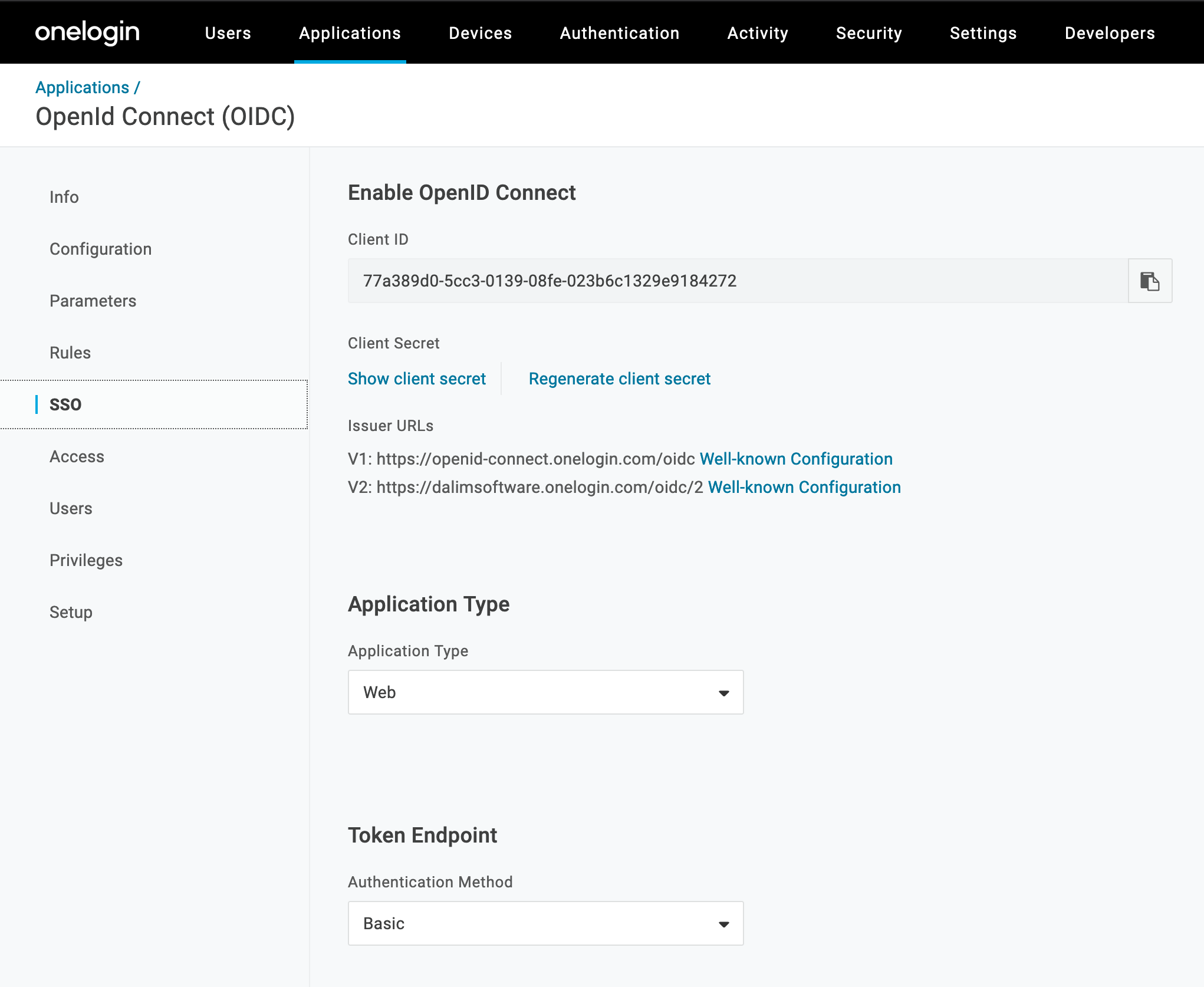
Please choose the V2 for the Well known configuration setup.
The useful information we have to note from that page are:
OIDCClientID 77a389d0-5cc3-0139-08fe-023b6c1329e9184272
OIDCClientSecret b2a---------------------------------------5879
OIDCProviderMetadataURL https://dalimsoftware.onelogin.com/oidc/2/.well-known/openid-configurationAll other parameters for this application can be left as default.
3- Setup Apache for SSO
For this part, we can follow the OpenID setup page here:
OAuth2 Single Sign-On for DALIM ES with Apache OpenIDC
Basically, you should follow these steps in a Terminal
- Install the Apache Web Server with:
yum install httpd
- Get the Apache module for OpenIDC for your Linux distribution
wget http://mirror.centos.org/centos/7/os/x86_64/Packages/mod_auth_openidc-1.8.8-7.el7.x86_64.rpm
- Install the OpenIDC module:
yum install mod_auth_openidc-1.8.8-7.el7.x86_64.rpm
- Enable the Apache Webserver at boot and start it
systemctl enable httpd.service
systemctl start httpd.service
- Verify that the OpenIDC files have got installed:
ls -l /etc/httpd/modules/mod_auth_openidc.so
ls -l /etc/httpd/conf.modules.d/10-auth_openidc.conf
- Enter the OPENIDC configuration into and Apache configuration file such as /etc/httpd/conf.d/openidc.conf
# STANDARD VIRTUAL HOST WITH OPEN ID
ServerName dalimes-ireland.es-cloud.com
#Securing Apache
RequestHeader set X-Forwarded-Port "" early
RequestHeader set X-Forwarded-Proto "https" early
Header set X-Content-Type-Options nosniff
Header edit Set-Cookie ^(.*)$ $1;HttpOnly;Secure;SameSite=Lax
Header always set Strict-Transport-Security "max-age=63072000; includeSubdomains"
Header always append X-Frame-Options SAMEORIGIN
#Raise time out for big file upload
KeepAliveTimeout 900
Timeout 5400
ProxyTimeout 5400
# Redirect URL to drive the user to the OneLogin SSO page
RewriteEngine On
RewriteCond %{REQUEST_URI} !^(/info.php|/oidc.*|/Esprit.*|/Latitude.*)
RewriteRule (.*) https://dalimes-ireland.es-cloud.com/Esprit/public/sso.jsp [L,R=301]
# Standard Proxy Pass for ES
ProxyRequests Off
ProxyPreserveHost On
ProxyPass /Esprit http://localhost:8080/Esprit
ProxyPassReverse /Esprit http://localhost:8080/Esprit
ProxyPass /Latitude http://localhost:8080/Latitude
ProxyPassReverse /Latitude http://localhost:8080/Latitude
AuthType openid-connect
Require valid-user
AuthType openid-connect
Require valid-user
# OpenID settings
OIDCClientID 77a389d0-5cc3-0139-08fe-023b6c1329e9184272
OIDCClientSecret b2a---------------------------------------5879
OIDCProviderMetadataURL https://dalimsoftware.onelogin.com/oidc/2/.well-known/openid-configuration
OIDCRedirectURI https://dalimes-ireland.es-cloud.com/oidc/redirect_uri
OIDCCryptoPassphrase anypassword
OIDCRemoteUserClaim email
OIDCScope "openid email"
OIDCPassClaimsAs environment
#OpenIDC dummy URL to drive the user to the OpenID-Connect module
AuthType openid-connect
Require valid-user
Options -Indexes
# ES SSO URL to make ES drive the user to the OpenID-Connect module and define the mapping between the CAS-User Header variable and the field "preferred_username" of the Azure AD
AuthType openid-connect
Require valid-user
RequestHeader set CAS-User "%{OIDC_CLAIM_preferred_username}e" env=OIDC_CLAIM_preferred_username
# LogOut URL
<if "%{query_string} =~="" ddmsaction="LogoutAction/" &&="" %{query_string}="" !~="" oidc="false/"">
Redirect 302 "/Esprit/public/Login.jsp" "https://dalimes-ireland.es-cloud.com/oidc/redirect_uri?logout=https%3A%2F%2Fdalimes-ireland.es- cloud.com%2FEsprit%2Fpublic%2FLogin.jsp%3FDDMSAction%3DLogoutAction%26oidc%3Dfalse"
</if "%{query_string}></location ></location ></location ></location ></location >- Save the /etc/httpd/conf.d/openidc.conf file
- You may be obliged to set the Apache ServerName variable in the main config file /etc/httpd/conf/httpd.conf
- Restart Apache
apachectl restart4- Setup ES for SSO
Here we need ES to authorize Single Sign On logins for the users belonging to the org unit matching to our AD.
It is not more complicated that ticking the box "Allow Single Sign On Authentication" under the Security options of your Organisational Unit in ES.
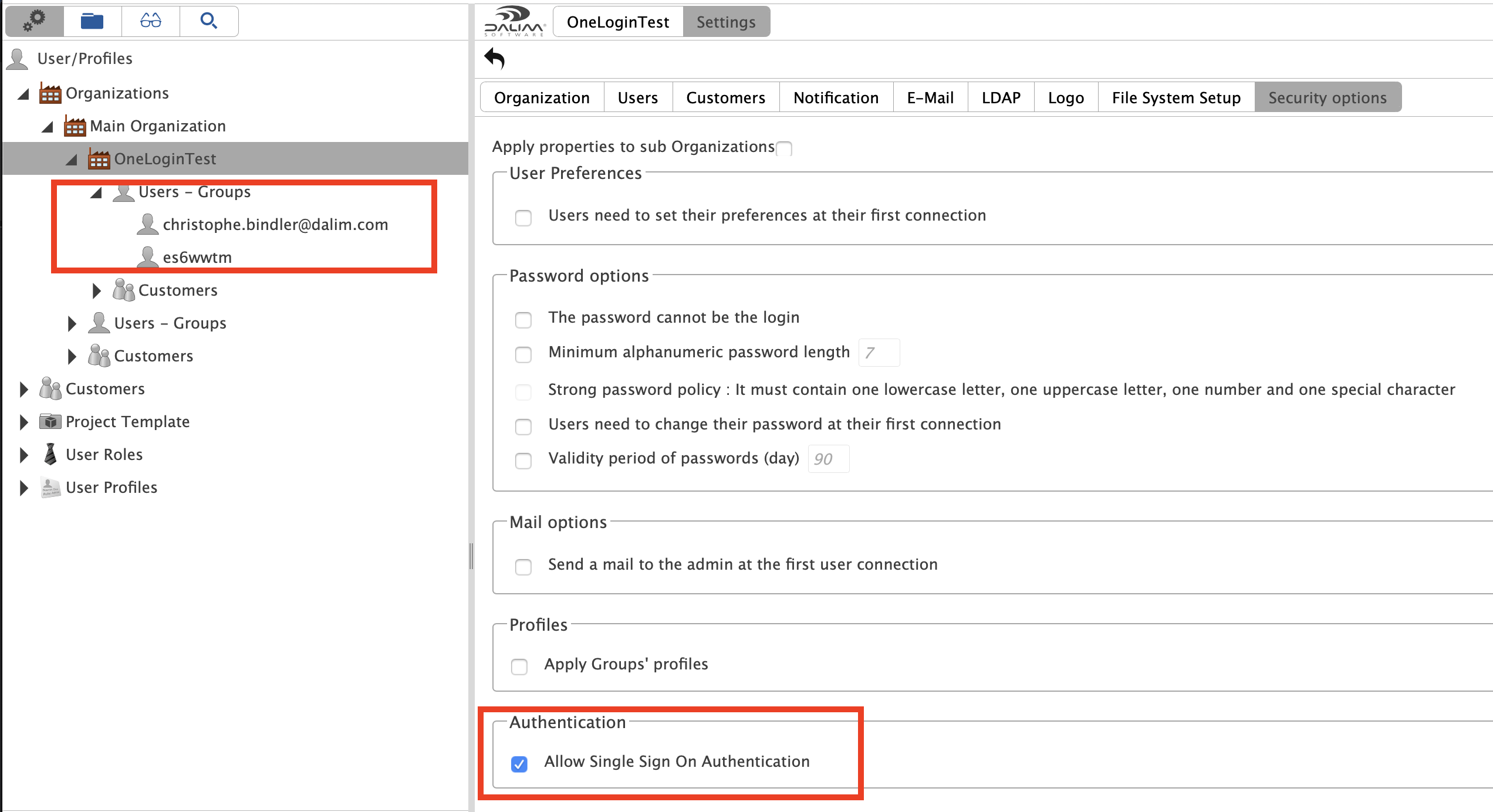
Please note as well that the users must exist in ES and with the appropriate user name !
Finally, in the config file /symlnks/common/tomcat7.0/bin/env.sh, please consider to disable the condition of use at first login of the users by adding this line:
JAVA_OPTS="$JAVA_OPTS -Dcom.dalim.conditionofuse=false"It is not mandatory but as your users already went through a hardened login protocol and possibly through the SSO condition of use page, you may not request them to approve again some condition of use.
A Tomcat restart is required now:
/symlnks/common/services/tomcat restart5- Allow your users to use the application
The DALIM ES Server is ready.
Let's go back to OneLogin to now authorize the users to use our Application created at step 2 of this document.
Here you can select a user and under the "Applications" tree entry, you can add the Application "DALIM ES OpenId Connect (OIDC)"
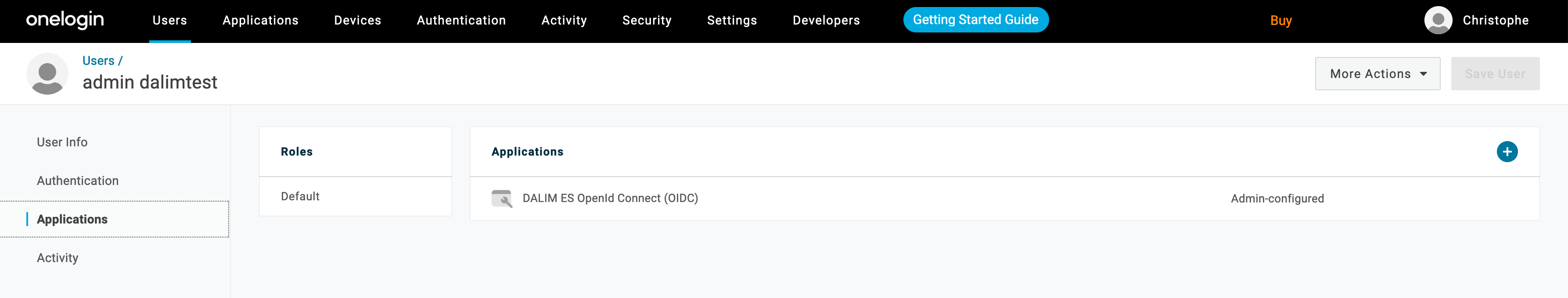
Save the changes and you are done for that user.
You can automate the access to an Application at creation of users in OneLogin. For this, you can create roles and groups for example.
Here in the default role, we have bound it to our Application.
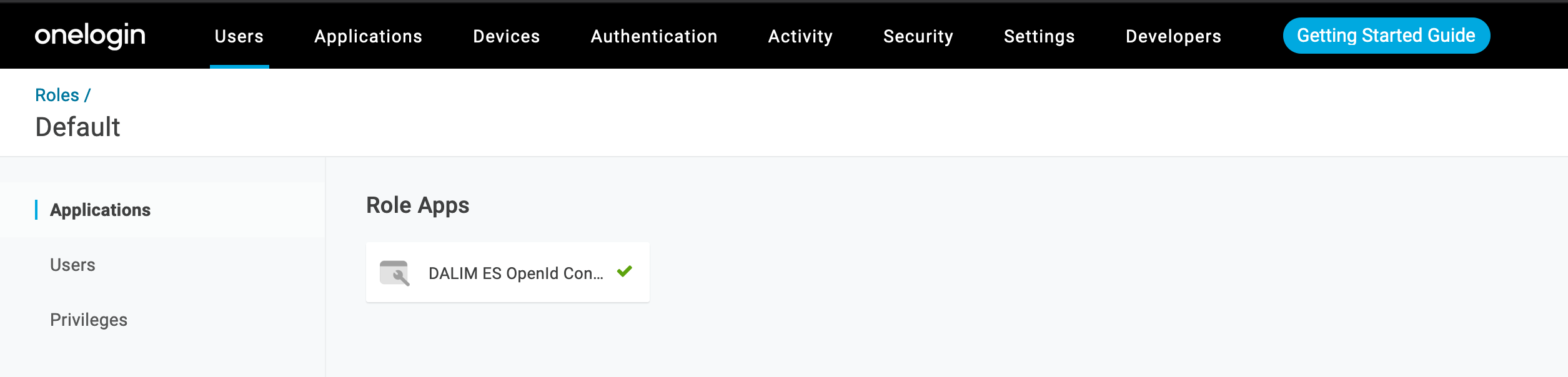
Now that our user is allowed to use the OpenIDC Application, we can do a first test in ES.
As our Apache is configured to redirect everyone going to its root URL to the SSO page, we just type this URL in our web browser:
https://dalimes-ireland.es-cloud.com/
As configured in Apache, we will then get redirected to:
https://dalimes-ireland.es-cloud.com/oidc/redirect_uri
This page will then get us to the OneLogin authentication page where you will have to enter your user name and password such as set in your Azure AD or in your OneLogin software if the users have been created inside OneLogin directly.
Once Authenticated in OneLogin, OneLogin will redirect you to the ES web site and get you logged in with your default user profile:
In the majority of the case, if this step fails, it is simply because the user name within ES does not match the user name in OneLogin or in your Azure AD.
For making sure about this, you can use the development tool of you web browser to inspect the CAS-User variable passed in the HTML page to DALIM ES.
You can as well enable the tomcat access log valve in /symlnks/common/tomcat7.0/conf/server.xml by uncommenting the AccessLogValve and adding a specific log that gets the CAS-User information:
<Valve className="org.apache.catalina.valves.AccessLogValve" directory="logs"
prefix="localhost_access_log." suffix=".txt"
pattern="%h %l %u %t "%r" %s %b %{CAS-User}i %{CAS-User-Profile}i" />
Once this change has been saved, please restart Tomcat and try again to log in to ES.
This time the Tomcat Access log file should show you the CAS-User content.
6- Enforce security with MFA and Onelogin protect App
To enable Multi Factor Authentication, you can go to the Security tab and create a new policy which will use the OneLogin protect OTP factor
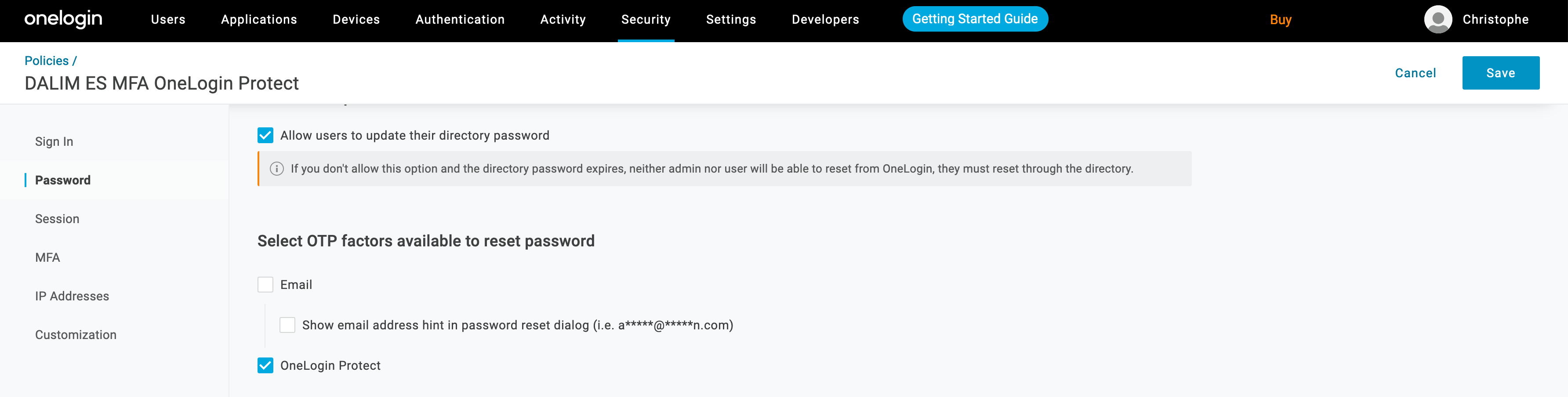
Under the MFA menu entry, please enable all necessary functions to force the MFA authentication:
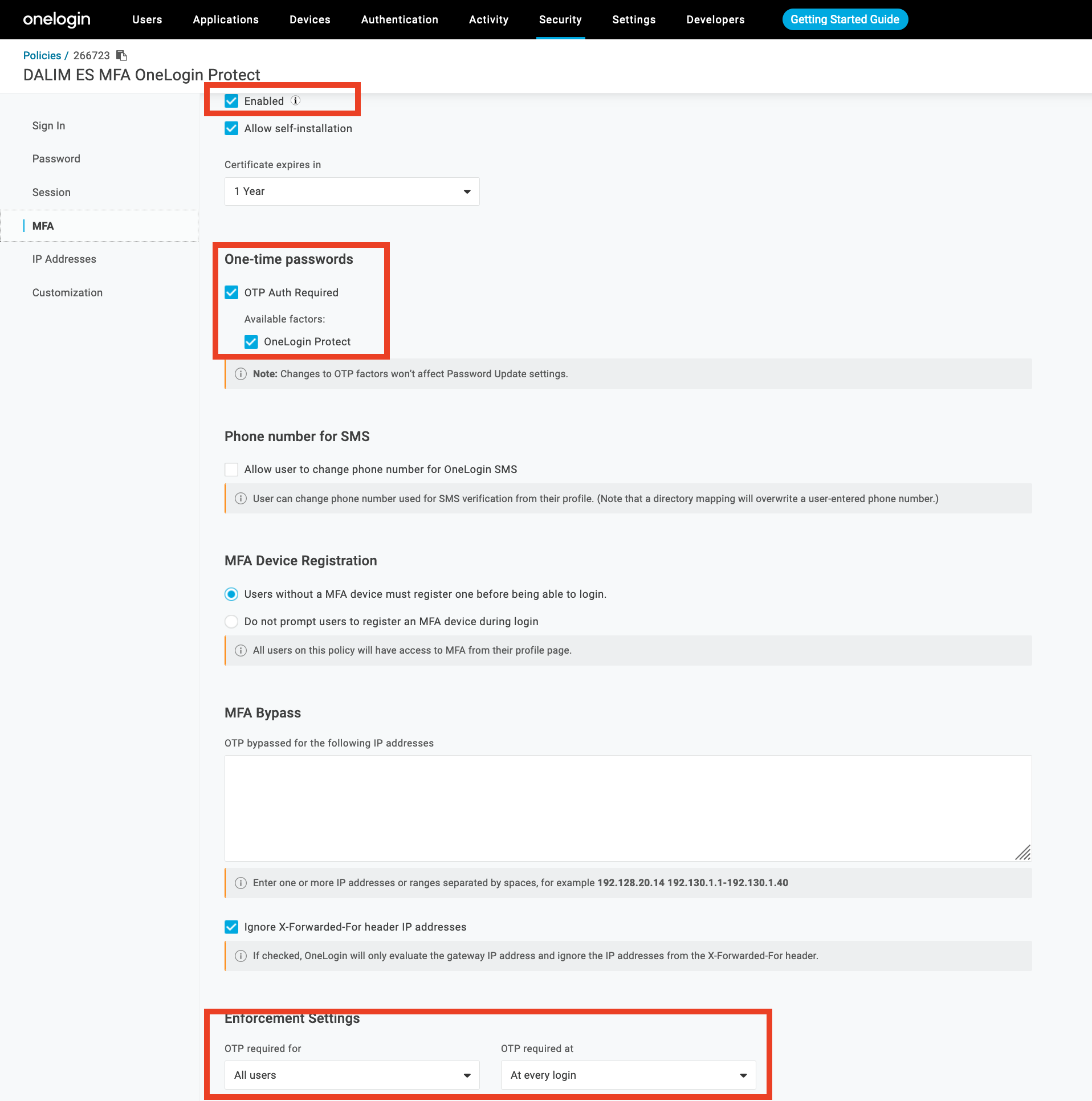
Once your policy is configured and enable for your user, the next time you will try to hit the ES web site, OneLogin will ask you for login + password and to setup your OneLogin Protect app on your mobile phone.
Starting from now, your DALIM ES login is secured with MFA !
Congratulations !